Once upon a time, in the bustling digital city of Byteville, transactions were the lifeblood that kept everything ticking. But just like in any great metropolis, without proper security, chaos would eventually seep in. Byteville had enterprising citizens who understood this all too well and thus began the grand quest for the holy grail of online shopping: “authentication mechanisms for transactions.”
Read Now : Risk Assessment For Logistics Networks
The Cool Evolution of Authentication
Alright, let’s be real. Back in the day, those passwords were the kings and queens of security. But in today’s wild digital jungle, basic passwords are like those floppy disks (yeah, remember them?). They’re kinda dated, right? So, in rides the cavalry of authentication mechanisms for transactions, bringing a sleek style and throwing shade at vulnerabilities. Picture multi-factor authentication, where you gotta confirm your identity via email or text. It’s like having a security squad watching over you! And then there’s bio-auth, which lets you just wave your hand or gaze into a scanner to do your biz. All this wizardry keeps your stash safe from the bad guys lurking behind their keyboards.
The Anatomy of Modern Authentication
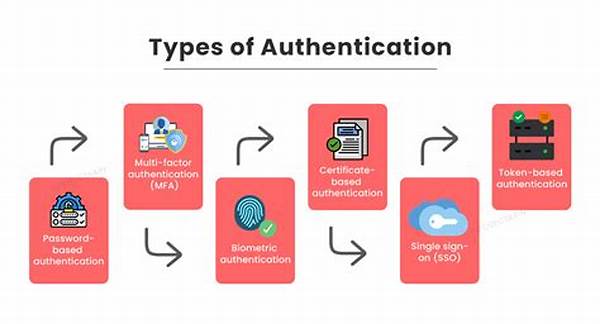
1. Multi-Factor Authentication (MFA): Mixing passwords with a sprinkle of extra sauce, like codes sent to your phone. It’s the “belt and suspenders” approach of authentication mechanisms for transactions.
2. Biometric Authentication: Your face, fingerprint, or even your voice is the password. It’s like turning your body into the key, so cool, right?
3. Token-Based Authentication: Devices or apps that provide a one-time password. They’re like secret agents ensuring only the right dudes get in.
4. Behavioral Analysis: This one’s sneaky smart. It watches your habits, like typing speed or mouse movements. It’s like having AI paparazzi following you.
5. Zero Trust Model: Universal level of paranoia, needing verification at every step. It’s like a bouncer constantly asking for your ID in a club of authentication mechanisms for transactions.
Why All Transactions Need a Fort Knox-Level Defense
So, ever tried pulling off a smooth transaction only to get stuck in the mud because someone hijacked your deets? Yeah, that sucks big time. Using authentication mechanisms for transactions is like wearing armor. They decided to take things ‘next level’ by upping the game with advanced techie stuff. As transactions grew, the need for locking things down tight was obvious. Hackers everywhere started trying their luck, thinking they could swipe data stealthily, like digital ninjas. But when authentication got serious, these crooks hit a wall. Imagine you’re chilling on a sunny beach, but worry-free because these mechanisms have got your back. That’s where we are now, living in a world where your data isn’t just guarded—it’s fortified. Oh, and did I mention the immense relief it gives businesses? They’re flourishing because customers know they’re safe, and everyone’s jazzed about transacting in this brave, new secure world.
Read Now : “litigation Drawbacks In Intellectual Property”
Diving Deeper into Tech Wonderland
In Byteville’s suburbs, tech whizzes are busy crafting what’s basically magic—but grounded in code. Imagine magic carpets that don’t fly on spells but on bytes: we’re talking authentication mechanisms for transactions. This wonderland includes gadgets and processes that keep your moolah safe. Dive deeper into this geeky world where every transaction is guarded by invisible knights of encryption. Encryption, dear friends, is like wrapping your message in an unbreakable box. As you secure your every move with these wonders, you step deeper into a realm where safety isn’t just priority number one—it’s a lifestyle. The blend of certificates, licenses, and security protocols make sure these mechanisms dance to a rhythm that only you know. No snoopers allowed. Byteville’s creative geniuses are hard at work, ensuring that your world operates without a hitch, seamlessly merging tech brilliance and peace of mind.
Unlocking the Secrets Behind the Firewall
To those on the outside, the fortress of online security might look like military covert ops—but hey, we’ve got the inside scoop. At the base of this security mountain lies authentication mechanisms for transactions. Think of them as digital sheriffs, keeping the peace as data crosses the wild web frontier. From facial recognition gatekeepers to cutting-edge algorithms that peek and poke under the hood of each digital interaction, these systems make sure no funny business goes down. As tech gets smarter, those nasty data breaches, phishing scams, and sneaky hacks fade into the background. Because as our tales of uneven access wane, we lean into the freedom of swiping, tapping, and clicking with zero fear. Embrace it, celebrate it, and most importantly, understand it. Because behind every seamless transaction is a labyrinth of neat coding wizardry designed to keep everything kosher and chaos at bay.
Riding the Waves of Digital Transactions
Let’s hit the throttle and skim across the digital waters of online purchases. In this realm, authentication mechanisms for transactions are like lifeboats, keeping every click, swipe, and tap afloat. Picture this: you’re snagging that limited-edition item, knowing your deets are snug. It’s not just about snapping up goodies, it’s about the whole dang vibe of trust and smooth sailing. Every time we engage in these transactions, we’re not just conducting business—we’re dancing, digitally at least. Grooving through processes and mechanisms that are crafted not just to protect us—but propel us. It’s a whirlwind where those authentication rituals become magic moves ensuring our purchase party doesn’t come crashing down in chaos.
A Summary of How Authentication Locks Everything Down
To sum it all up, these advanced authentication mechanisms for transactions are our digital watchdogs. They help keep our money safe and our information even safer. Think of them as the bouncers at the busiest club, with velvet ropes and exclusive guest lists. Back in the day, relying just on passwords was like using a basic lock on a treasure chest; now we’ve evolved. Multi-factor authentication, biometrics, and other mechanisms have revolutionized online security. The aim is simple: no more unwanted gatecrashers. With each advance, hackers are made to think twice, giving peace of mind to everyone using online platforms for their day-to-day dealings. As we wrap up, remember, while we’re all in a constant hustle, these authentication mechanisms are tirelessly keeping your data safe. Their mission? Ensuring every transaction is hassle-free and secure, like a silent guardian ensuring nothing ever goes wrong in Byteville’s interconnected realm.