Once upon a digital time, in the heart of the bustling cyber world, a company named Tech Fortress realized they needed to arm themselves against potential cyber threats. The CEO, Sandra, had been kept awake too many nights by whispers of hackers and breaches. With dreams of shields and firewalls, she set forth on a mission to ensure the safety of her company’s digital kingdom. And that’s when she stumbled upon a magic formula, something known as the “vendor cybersecurity evaluation process.”
Read Now : Safe Development Of Decentralized Applications
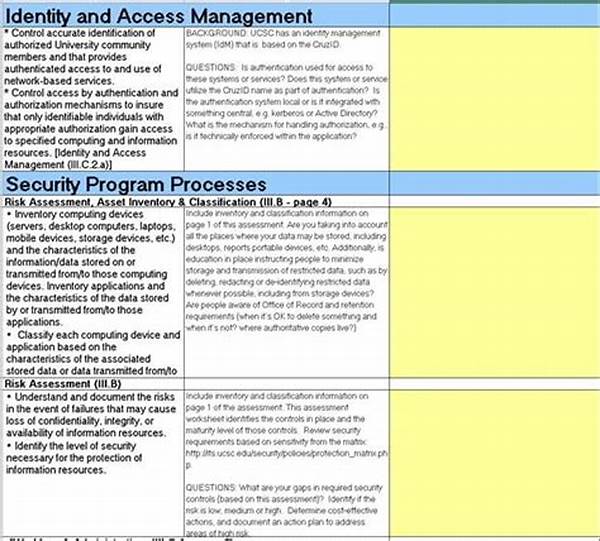
Understanding the Vendor Cybersecurity Evaluation Process
So, you’re chillin’ with your morning coffee, scrolling through emails when it hits you. The vendor cybersecurity evaluation process isn’t just a fancy term; it’s like the secret handshake to joining the cyber-safe club. You gotta know your stuff to vibe with the best vendors, right? So, here’s the deal: if you’re working with third parties, you better make sure they’re not secretly inviting cyber trolls into your system. This whole evaluation gig? It’s like speed dating for tech nerds — quick yet thorough. Picture this: you’re analyzing their security protocols, checking for vulnerabilities like a pro detective. It’s all about making sure your partners aren’t letting any shady characters through the digital gates. And trust me, once you get the hang of it, you’ll be the king or queen of the vendor cybersecurity evaluation process, owning the cyber scene.
The Core Elements of the Vendor Cybersecurity Evaluation Process
1. Initial Screening: The first impression matters! Ensure vendors meet basic security requirements before diving deeper.
2. Risk Assessment: Check out their security stance to see if they’re rock solid or if there’s a need to raise a red flag.
3. Compliance Check: Are they following the industry rules, or are they rebels without a cause?
4. Technical Evaluation: Get your nerd glasses on and dive into their tech specs to uncover any lurking dangers.
5. Continuous Monitoring: Like a hawk, keep an eye on vendors to ensure they’re still in line with your standards.
How to Implement the Vendor Cybersecurity Evaluation Process
Implementing the vendor cybersecurity evaluation process is like putting together a cyber party guest list. You don’t just invite anyone, right? You gotta know who these vendors chill with, their security histories, and if they vibe with your security policies. Start by getting your tech team to shortlist vendors who pass the initial sniff test. Then, dive deeper and analyze their cyber-defenses like a tech geek on a mission. Partner up with your IT rockstars to assess whether these vendors are playing by the rules or skating on thin ice. By constantly monitoring their security scene, you keep everything in check. It’s all about building a cyber-friendly squad you can trust.
Read Now : Innovative Blockchain Applications In Gaming
The Benefits of a Thorough Vendor Cybersecurity Evaluation Process
Embarking on the vendor cybersecurity evaluation process is like hitting the jackpot in a cyber lottery! First off, you dodge those nasty cyber bullets that could potentially wreck your rep. You also boost your company’s IT mojo by working with top-notch vendors who know their cyber onions. It’s all about keeping that data fortress solid and preventing any sneaky data breaches. And hey, your wallet’s gonna thank you too, because you save big bucks by avoiding costly security meltdowns. Plus, your clients will love the peace of mind, knowing you’ve got their backs in this digital jungle.
Challenges in the Vendor Cybersecurity Evaluation Process
Even in a world of cyber superheroes, challenges lurk in the vendor cybersecurity evaluation process. Sometimes, digging deep into vendors’ security practices can feel like searching for a digital needle in a haystack. Maybe you don’t have enough manpower to scrutinize every detail, leaving some potential threats flying under the radar. Plus, some vendors play it cool with their security measures, making it tough to see their vulnerabilities. And let’s not forget those ever-changing tech trends—what was secure yesterday might be hackable tomorrow. But with patience and a savvy crew, these challenges can transform into just another fun level in the cybersecurity game.
Keys to Success in the Vendor Cybersecurity Evaluation Process
You know what they say, “Preparation is key!” To ace the vendor cybersecurity evaluation process, you gotta embrace a proactive mindset. Start by keeping tabs on industry trends that could shake up your vendors’ security strategies. Collaborate with your security team to design a solid evaluation framework that casts a wide net over potential risks. By maintaining open lines of communication with vendors, you’re more likely to sniff out any security red flags early on. And remember, success is all about keeping that cyber radar sharp and your digital walls unbreakable.
Conclusion: Embracing the Vendor Cybersecurity Evaluation Process
In the end, the vendor cybersecurity evaluation process is your golden ticket to a safer tech space. It’s like having a digital bodyguard that ensures your company doesn’t get punked by nasty cyber threats. You get to choose your allies, vetting each one with precision, until you’ve assembled a squad that truly gels with your safety standards. And yeah, it might feel like a lot of cyber hoops to jump through at first. But once you’ve got a grip on the process, it’s as sweet as claiming that high score in an epic video game. Keep those security instincts sharp, and you’ll be the champion of your digital fortress.