Ever wondered what keeps our online world safe from prying eyes and nasty hackers? Picture this: a bustling city of data where every piece of info travels through intricate pathways, each guarded by invisible but rock-solid gates. This is the story of how protocol integrity with encryption techniques became the unsung hero of our digital age.
Read Now : Supporting Female Innovators In Blockchain
The Intricate Dance of Data Guarding
In the cyber universe, where every byte is a prized possession, ensuring its safe journey is like juggling flaming torches. Enter the world of protocol integrity with encryption techniques! Picture them as a squad of elite bodyguards, ever-ready to protect and serve. They make sure that your secret messages to your bestie or those annoying work emails stay private and secure.
Yeah, encryption may sound like a geeky word, but it’s the shield that keeps your data intact. Imagine your favorite pasword—a complex, uncrackable code—always doing a secret dance to keep eavesdroppers at bay. That’s encryption doing its magic! It ensures that data stays fab and flawless, without letting rascals sneak a peek or mess things up. By the way, did you know these data packets attend encryption parties before they head out? They love a bit of security glam! Checking, rechecking, and securing—they’ve got it covered to make sure that when your data arrives, it’s in tip-top shape, fresh from its protocol integrity with encryption techniques journey.
Secrets Behind the Hidden Fortress
1. Encryption Types: Think of these as different secret languages. Each has its own vibe to trip up unwanted guests.
2. Integrity Checks: They’re the bouncers, making sure nothing sneaks in or out without getting a thorough check.
3. Data Authentication: It’s like a digital ID, proving that your data is legit and coming from the right source.
4. Error Detection: This tech sniffs out mistakes and patches them up before you even notice anything amiss.
5. Secure Keys: The ultimate VIP pass that only select info gets to hold. It’s exclusive and extremely protective!
Unpacking Protocols’ Secret Sauce
When it comes to keeping online vibes chill and drama-free, protocol integrity with encryption techniques is the ultimate bestie. Imagine every TikTok you upload, every meme you share—it’s all a private party just for you and your friends. These encryption techniques? They’re like that one friend who always manages to avoid spilling tea, no matter how wild things get. They’re the reason your precious data stays yours, not your nosy neighbor’s.
And here’s the cool thing: these digital fortresses are evolving, constantly learning new moves to outpace troublemakers. New algorithms pop up like viral TikTok dances, ensuring protocol integrity is always in the loop. From symmetric to asymmetric encryption, there’s always a strategy to stay secure. Those pesky hackers trying to sneak in? They’re left wandering a maze with protocol integrity’s clever tricks. It’s the ultimate spy movie, but you always win!
The All-Seeing Eye of Protocols
Protocol integrity with encryption techniques is like the ultimate sibling duo, always having each other’s backs. Ever used WhatsApp or Signal? They’re solid proof that encryption is every modern-day app’s BFF. Their handshake is more than a friendly wave—it’s an unbreakable bond, ensuring messages zoom between friends like they’re coded whispers only the right ears can hear.
1. Zero-knowledge: An app’s promise never to spill your deets. It won’t even let you know what it knows because—shock—it doesn’t!
2. Forward Secrecy: Old messages? Forget about it! No hacker is cracking those forgotten whispers of the past.
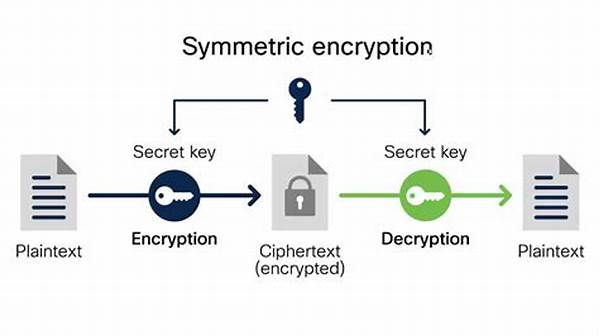
3. Symmetric Encryption: Like sharing secrets with just one bestie because two can keep a secret if one of them encrypts.
Read Now : Blockchain Developer Gatherings Dubai
4. Asymmetric Encryption: Picture a postcard with a secured mailbox—one key sends it, another unlocks it.
5. End-to-End Encryption: Your data takes a solo trip without unwanted hitchhikers. Safe and sound all the way.
6. Quantum-safe encryption: Just in case science goes all “Avengers” and bends the rules of reality, we’ve got encryption even a quantum computer can’t trespass.
7. Perfect Forward Secrecy: Changing keys just like changing outfits—keeps the look fresh and invader-proof.
8. Public Key Encryption: The not-so-secret, secret handshake. Only those who know the proper wave can say, “Hello!”
9. Transport Layer Security (TLS): Like the chill bodyguard who ensures data gets from A to B without any road bumps.
10. Hash Functions: Tiny, digital breadcrumbs ensuring nothing goes MIA without leaving a trace.
Living in the Secure Lane
Chillin’ in the digital universe requires more than just knowing the latest viral trends—it’s all about protocol integrity with encryption techniques. Imagine sending off your glossy selfies into the cloud, devoid of worry. That’s the freedom these encryption wizards provide, keeping every swipe, click, and tap locked like a treasure chest. And while hackers craft their dastardly traps, these techniques skate circles around them, eyes always on the prize: your privacy.
Think of encryption as the trendiest fashion statement your data can wear. As technology zooms forward, these techniques are like the evergreen denim jacket, constantly in style and robust enough to match any trend. Flexible yet firm, it evolves with every click, guaranteeing peace of mind while scrolling through your fave apps, blasting out tweets, or vibing on your Spotify playlists. Protocol integrity with encryption techniques is the silent prom king everyone votes for—dependable, cool, and the best dance partner!
The Ultimate Digital Wingman
In this brave new digital age, you need protocol integrity with encryption techniques as your numero uno wingman. They ensure every convo between pals or loved ones stays yours alone, free from outside noise. Next time you’re sending a DM or snapping a quirky video, remember the unseen heroes working tirelessly to keep that data locked tight.
The future’s looking bright with encryption as the digital baby’s blanket. It’s the ultimate combo of strength and style, the must-have accessory for any netizen. As we zip through pixels and streams, carrying imaginative content, know that encryption stands firm, shoulder to shoulder with protocol integrity, like unparalleled guardians. Together, they make sure that our digital escapades are as safe as a mom’s hug on a stormy night.