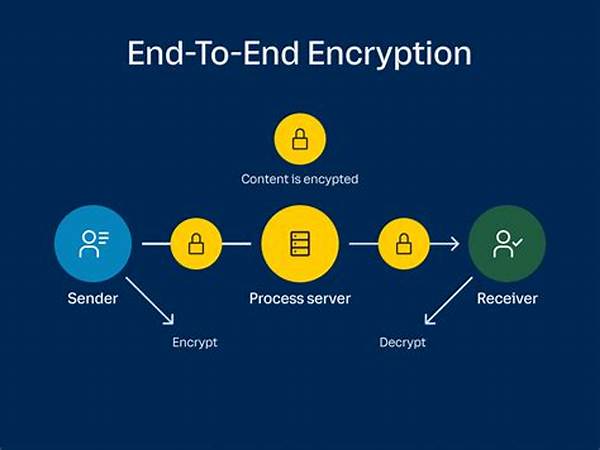
Once upon a digital realm, where privacy seemed like a fairy tale, cryptographers came up with a spell called ‘end-to-end encryption.’ They promised a world where information could securely travel from one magic device to another without being spied upon by evil digital sorcerers. But as with any powerful spell, there were always those who wanted to crack it. That’s where end-to-end encryption integrity measures came into play, ensuring that the magic would not be broken and vast digital kingdoms would remain safe and sound.
Read Now : Block Validation Process Optimization
The Magic Behind End-to-End Encryption Integrity Measures
Alright, let’s break it down like a late-night chat over nachos. You know how when you send someone a private message, you want it to be just that—private? End-to-end encryption (E2EE) has become the ultimate guard dog ensuring no shady peeps can eavesdrop on your digital convos. But here’s the scoop; encryption isn’t enough by itself. The magic trick is making sure it stays watertight—cue the end-to-end encryption integrity measures. These bad boys ensure your encrypted messages aren’t tampered with en route. If someone even sneezes near your data, these measures will bark back, warning of any rogue actions. So, the whispers behind those 1s and 0s remain as secretive as a squirrel with a stash of nuts.
Now, imagine sending a super secret love note that only your crush can decipher. If someone tries to mess with it along the way, the end-to-end encryption integrity measures act as your backstage bouncers. They spot the mischief-maker, donning a detective hat to ensure nothing shady hits your inbox. In the realm of digital communication, they’re like the ultimate truth detectors, making sure nobody adds a sneaky ‘not really’ to your ‘I love you.’ Bottom line: with these measures, the digital veil remains untarnished, preserving the honesty of every secret shared.
Why End-to-End Encryption Integrity Measures Really Matter
1. Data Guardianship: Imagine a digital superhero protecting your data from foes. These integrity measures are the real MVPs, ensuring nothing messes with your cryptographic cipher.
2. Authenticity Check: Every message sent meets its digital doppelgänger. If there’s even a tiny mismatch, the system goes “no entry!”—integrity measures for the win!
3. Security Seals: Think of it as a wax seal on a letter. It proves your message is untouched by unauthorized peeps.
4. Tension Breaker: You’re at ease knowing your private stuff remains just that. Integrity measures kill the anxiety, letting you focus on the fun stuff.
5. Trust Builder: Ensuring messages stay as intended grows trust between users and devices—’cause who doesn’t love a trusty sidekick?
The Evolution of End-to-End Encryption Integrity Measures
Picture the early days of the internet like the Wild West with cowboys and chaotic shootouts. Folks realized they needed some peacekeepers to tame this chaotic digital world—thus entered end-to-end encryption integrity measures. Like a knight in shining armor, these measures kept messages pristine and ensured no Rambos could mess with your files. Besides keeping the peace, they’ve evolved, like a Pokémon, into more sophisticated sentinels of privacy.
Back in the day, things weren’t this locked down. Messages traveled through the ether exposed to snoopers who got their kicks from checking your deets. But times have changed, and today, it’s like having an invisible forcefield around your chats. End-to-end encryption integrity measures act as that cool friend who during a game night spots when someone tries slipping in a Joker card in Poker and calls them out. So, these measures aren’t just about keeping things secret; they’re the unsung heroes that make sure your story is straight and intact.
The Craft of Using End-to-End Encryption Integrity Measures
Jumping into the technical wizardry of end-to-end encryption integrity measures might sound like attending a calculus lecture you didn’t sign up for. But fear not, it’s simpler than it sounds. Here goes the debrief in a rad fashion:
1. The Key Exchange: This is the VIP ticket access. Keys are exchanged in a way that one can never simply guess or hack it. It’s like your super-secret handshake only you and your bestie know.
Read Now : Distributed Ledger For Ownership Authentication
2. Encryption and Decryption: Messages are turned into secret codes, then flipped back into original text once it reaches its spot—very Mission Impossible-like.
3. Integrity Checks: Picture sending a box with a fingerprint lock, and if opened, it alters the fingerprint—teensy details ensure your box stays secure.
4. Secure Channels: Your chat takes a safe, encrypted tunnel away from prying eyes—virtual invisibility cloak level awesome.
5. End-to-End Verification: Every step of the convo is verified like an endless sequence of high-fives ensuring it’s the real OG message.
More Insights on End-to-End Encryption Integrity Measures
Okay, let’s get deeper with it. Communicating safely shouldn’t feel like a covert spy mission (unless you’re into that kinda vibe), but it’s comforting to know your private life isn’t showbiz. End-to-end encryption integrity measures offer just that—they keep those nosy busybodies out of your convos. But here’s the kicker: they’re not just sprucing up texts; they’re becoming the standard in making sure privacy isn’t a 90s fad but more like the gold standard of our age.
You ever had someone go through your diary without permission? Massive no-no, right? Well, using these measures is like having a self-destruct mechanism in every entry if someone tries a sneaky peek. Yet, it’s all automatic; once you set your secure protocols, life becomes a zipline of secure exchanges. Whether texting, sending voice notes, or sharing a meme, end-to-end encryption integrity measures are your bodyguards ensuring every giggle, plan, or rant is just for you and those within your circle.
Final Thoughts on End-to-End Encryption Integrity Measures
Wrap this tech talk like a burrito: in our digital age, privacy’s king, and these measures make sure you’re the king or queen of your domain. End-to-end encryption integrity measures have evolved like a gripping Netflix series—each season more thrilling than the last, defending the sanctity of your messages. They stand tall, tech’s unsung warriors. If privacy were a rock concert, these measures would be the backstage passes everyone wants but only a dozen get.
To keep the digital dream alive, these integrity measures serve a buffet of safeguarding tools. They’re that buddy in high school who had your back against bullies—only now, they do it for your cyberspace life. So next time you send a meme or declare your undying love for pineapple pizza without fear of judgment, tip a hat to end-to-end encryption integrity measures. They’re the reason why the digital realm remains a secure place to groove, connect, and share your epic tales.