Once upon a time in the bustling world of the internet, where data zipped through wires faster than the speed of light, people realized they needed a way to make sure everything was legit. Enter the magic of digital signatures for protocol validation! Just as knights of old carried seals to prove their letters weren’t forgeries, our modern digital knights-errant rely on digital signatures to confirm their electronic missives are genuine. This isn’t just tech wizardry; it’s fundamental in making sure our online interactions are secure and trustworthy.
Read Now : Ai-driven Asset Verification Processes
Why Digital Signatures Matter
In today’s digital era, we all thrive on speed and accuracy. But what happens when you’re not sure if what you’re reading is authentic? That’s where digital signatures for protocol validation come into play. Imagine sending a love letter but not being sure if it’s delivered to your crush safe or sound. Scary, right? This is analogous to digital data without validation. Digital signatures act like your digital pinky promise; they ensure the data being exchanged is verified and untampered. Through technosavvy code and cryptography, digital signatures keep the vibe real, preventing any kind of tampering or mischief in data exchanges. No more stress about locas data breaches when you’ve got these bad boys in place!
Behind the Scenes of Digital Signatures
So how do digital signatures really work? Let’s break it down, shall we?
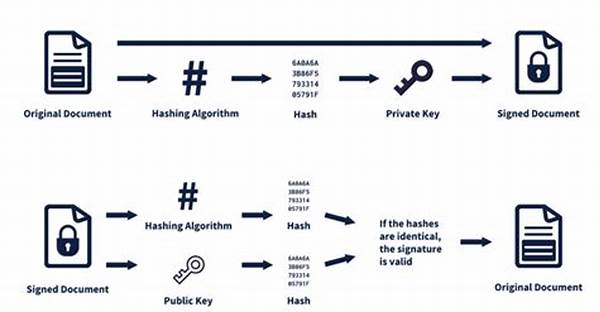
1. Cryptographic Keys: Think of these as the secret keys to your diary—only certain peeps can read your entries.
2. Hash Functions: This is like your secret handshake—unique and only shared with whoever you trust.
3. Public and Private Keys: Public is like your phone number and private is your unlock code. Keep that private key safe, fam!
4. Validation Process: This is the behind-the-scenes drama of authenticating the digital handshake. Legit af!
5. Certificates of Authority: These are like the bouncers at the club, ensuring only the real deal gets access.
How It All Comes Together
Okay, so you’ve heard about the nitty-gritty, but let’s talk about the vibe of digital signatures for protocol validation. Picture this: each step adds another layer of chill in the hot mess of online data exchanges, ensuring data vibes are in check. It’s like building trust in a relationship, one tiny step at a time.
Read Now : Bridging Logistical Inefficiencies Techniques
First, you’ve got the cryptographic keys handing out trust like candy on Halloween. Then, picture the hash function securing everything tighter than a freshman dorm party. Add those public and private keys for a sprinkle of exclusivity, ensuring only the trusted get in. Once all’s locked and loaded, the validation process seals the deal, waving off any sketchy stuff. Finally, the certificates of authority stand guard, making sure only those with the proper credentials waltz through.
Decoding the Tech Magic
Ever met someone at a party, and as soon as they say, “I’m in tech,” you nod and pretend you know their lingo? Well, digital signature for protocol validation is the nerdy love language. It’s about securing messages with cryptographic methods to ensure they haven’t been altered. The process guards against identity theft, digital forgery, and the general chaos the web can bring. It’s not just tech talk; it’s the secret sauce keeping our digital world spinning smoothly without turning into a dumpster fire of unverified misinformation.
The Everyday Importance
In today’s always-online world, digital signature for protocol validation is as crucial as that morning coffee. It kicks in the adrenaline of trust across sites and emails, ensuring businesses run smoothly and securely. Whether it’s banking, online shopping, or even government transactions, the stakes are high, and validation is that silent protector in the background. Without it, we’d be drowning in a sea of spam and fraud, constantly questioning if we’re dealing with a trusted source or a two-bit huckster. So, cherish these digital knights that keep our interactions safe, because they’re working ’round the clock like legends.
Securing the Future
So you’re probably guessing that digital signature for protocol validation is the unsung hero of our digital age, putting a lock on data insecurity and unverified chaos. As technology advances, this validation plays a crucial role in ensuring everything from our smart homes to global communications operate seamlessly. It’s no longer just about securing a message; it’s about securing the future, making sure our journeys into new tech realms are as suave and seamless as the world we dream about. With their help, the digital landscape is a trustworthy playground where innovation thrives without the fear of step-back-edness.
Wrapping It Up
Alright fam, here’s the download: digital signature for protocol validation is the backbone of our digital reality. Every bit of data zooming across cyber highways relies on these signatures to prove it hasn’t been tampered with. It’s like making sure your online life doesn’t ghost you with faulty info. Sure, it’s all ones and zeroes, but with the right validation, it becomes a plotline of safety and trust running behind our screens. Keep vibing with your digital tools and remember, they’re more than just lines of code running a script; they’re the unsung digital wizards making your online experience magical and secure.