Once upon a time in the digital age, where everything from groceries to grand secrets seemed to be floating in the cloud, there was this magical thingamajig called the blockchain—a distributed ledger as they called it. This wondrous chain of blocks promised transparency, trust, and tamper-proof transactions. But every great story needs its hero and villain, right? Here, the heroes wore armor in the form of distributed ledger security measures. As digital whispers grew about these measures, it was clear they were the silent guardians ensuring the integrity and trustworthiness of these virtual diaries. Let’s dive into the fascinating world of these cyber knights.
Read Now : End-to-end Voting System Encryption
The Basics of Distributed Ledger Security Measures
Picture this: a vast digital ocean with countless bits of data floating around. Now, imagine securing this ocean with a mystical net called security measures. Yeah, sounds epic, right? Distributed ledger security measures are like the bouncers at the coolest club in town, making sure no shady characters mess up the vibe. They’re all about ensuring data is legit, not tampered with, and oh-so-secure. So, whether you’re using blockchain to buy coffee or seal million-dollar deals, these measures are the unsung heroes making sure everything stays squeaky clean.
Imagine your favorite celebrity has a super exclusive, all-access party—only the best, no drama kings or queens allowed. In the realm of blockchain, the distributed ledger security measures are those party bouncers checking every VIP’s invite. These measures watch over the digital dance floor, making sure no unwanted guests crash the party and everything runs smoother than a fresh jar of peanut butter.
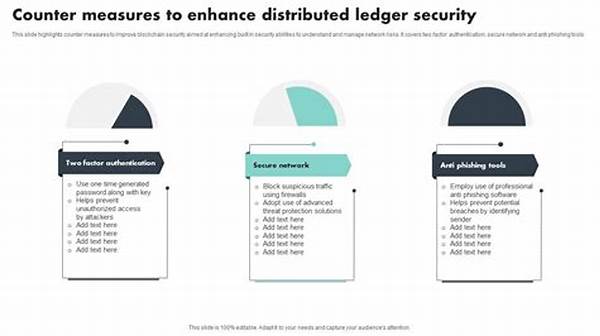
Key Components of Distributed Ledger Security
1. Encryption Magic: Keeping data super-secret, only for those with the golden key.
2. Consensus Protocols: Like a digital group hug that ensures everyone agrees.
3. Identity Wizards: Verifying all players to keep imposters at bay.
4. Audit Trails: The meticulous scribe recording every digital footstep.
5. Smart Contracts: Automated gatekeepers ensuring no funny business.
How Distributed Ledger Security Measures Work
Got your curiosity piqued? Let’s dive into the digital wizardry! Distributed ledger security measures are like that chill DJ who keeps the party vibes on point—ensuring everything clicks in rhythm. So, you got this digital ledger, right? To keep it super reliable, a whole squad of hackers, nerds, and digital detectives work tirelessly. They hash, encrypt, and verify each bit of data to keep any funny business outta there. Every party (transaction) is vetted like celebs on a red carpet, making sure nothing but legit info struts its stuff.
Behind the scenes, these measures flex their cyber-muscles. They run deep audits, like Sherlock Holmes but in the matrix, ensuring everything’s kosher. And let’s not forget the advanced encryption—a mystical barrier that keeps nosy parkers out. To top it all off, there are these nifty consensus protocols where everyone has to be on the same page, or block, you could say. Now, ain’t that an impressive show of digital security muscle?
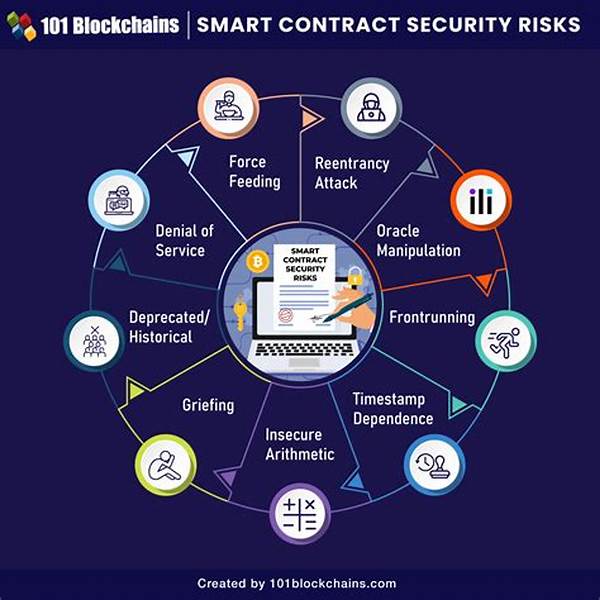
Common Threats to Distributed Ledger Security and How to Beat ‘Em
Threats? Oh, you betcha! The digital realm is like the wild west of tech. But with the right distributed ledger security measures, it’s totally manage-a-bull. Here’s how:
1. Sybil Attacks: Fake identities causing chaos. Beat with strong ID checks.
2. 51% Attacks: Majority takeover. Dodge it using mixed consensus protocols.
3. Phishing Schemes: Crafty emails fishing for data. Counter with cyber-smarts.
4. DDoS Attacks: Traffic jams trying to crash the party. Use network shields.
Read Now : “techniques For Ip Conflict Prevention”
5. Malware Invasion: Unwelcome guests. Set up mighty antivirus defenses.
6. Private Key Theft: Stolen digital diary keys. Protect with layered encryptions.
7. Data Breaches: Info leaks. Encrypt everything like Fort Knox.
8. Smart Contract Bugs: Glitches in code. Routine audits keep things tidy.
9. Transaction Malleability: Tricky alterations. Regular checks fix that.
10. Replay Attacks: Old data in new tricksters. Timestamp magic beats it back.
Implementing Effective Distributed Ledger Security
Implementing distributed ledger security measures is like teaching a turtle to moonwalk—it’s a delicate process, but oh-so-rewarding. First, you gotta lay the foundation with rock-solid protocols. Think of them like golden rules that keep everyone in check. Then, juice up your system with state-of-the-art encryption, making it as impenetrable as an ’80s action hero’s fortress. And, don’t forget to throw in a pinch of regular audits to ensure everything’s sweeter than grandma’s cookies.
Imagine it like assembling your dream team of digital security—each blend of technique amping up the overall effectiveness of your ledger fortress. Regular updates, bug bounties, and a commitment to game-changing research keep your system on top of its game. It’s all about ensuring you’re not just keeping up with threats but staying miles ahead. And that, my friend, is how you cover your digital back better than any secret agent on a mission.
The Future of Distributed Ledger Security
Now let’s time travel just a little bit. The future of distributed ledger security measures is brighter than a 90s dance floor jam! We’re talking AI-integrated defenses, adaptive security layers, and quantum-proof protocols that sound like they’re straight outta a sci-fi film. These measures are constantly evolving, just like your ex’s Spotify playlist—always switching it up, always keeping things fresh. Just imagine, one day, even our toasters might be hardwired with these unstoppable defenses!
In this soon-to-come world, distributed ledger security measures will be more than just tools—they’ll be like digital guardians, adapting in real-time to fend off threats. So kick back, stay tech-savvy, and watch as these measures continue their epic quest to protect our data kingdoms. With security measures as awesome as these, the future of digital interaction is going to be nothing short of a thrilling ride.
Wrapping Up Distributed Ledger Security Measures
By now, you can probably picture distributed ledger security measures like the elite crew in an action blockbuster—each member uniquely skilled, yet working in perfect harmony. They encrypt, verify, and outsmart every sneaky saboteur lurking around. It’s like having your digital cake and eating it too, with a side of peace of mind. Yeah, they might operate behind the scenes, but their impact? Monumental.
As digital landscapes continue to shift and sway, these security measures will remain the cornerstone of trust and transparency. So, whether you’re an all-in techie or someone just dipping their toes, remember that distributed ledger security measures are the unsung heroes keeping order in our wild, wonderful digital frontier. And that’s a wrap on our tale of these incredible cyber guardians!