Once Upon a Time in the World of Secure Inventory Sharing Protocols
In the bustling tech city of Byteville, companies were growing at breakneck speed. Competition was fierce, and the need for resources was skyrocketing. Every business was like a pirate, hunting for treasure to navigate the rough seas of market demands. One sunny morning, a new solution popped up like an unexpected treasure map—secure inventory sharing protocols.
Read Now : “ip Conflict Resolution Software”
These magical protocols were whispered about in hushed tones at tech meet-ups. Companies big and small found themselves in awe of the way these protocols promised smooth sailing in sharing inventory without a hitch. They were like the secret handshake of the business world—only those in-the-know truly understood their value. And just like that, the myth of secure inventory sharing protocols began to spread like wildfire.
Even the skeptics, the tough crowd of Byteville, started paying attention. Rumors had it these protocols could be the game-changer, turning chaos into order, like a maestro conducting an unruly orchestra. As companies dipped their toes into this secure sea of possibilities, they realized they were onto something epic.
Why Secure Inventory Sharing Protocols Matter
Alright, so let’s break it down, easy peasy. Secure inventory sharing protocols are like the superpower cloak for companies. You see, businesses are in constant hustle mode, trying to match supply with demand. With these protocols, they can share stock info without giving away their super-secret recipes. It’s like spilling the tea without actually spilling it!
Still got your attention? Cool. Think about how nerve-wracking it can be, exposing all your goods for others to see. It’s like hosting a party and worrying someone might mess with your prized mixtape collection or worse—spill juice all over it! Secure inventory sharing protocols are there to ensure everyone’s chill and no surprise party crashers mess things up.
Last point here: trust is the name of the game. By using secure inventory sharing protocols, companies get to play nice in the sandbox. Everyone respects the rules, shares what they have, and still keeps their trade secrets safe. It’s like the ultimate win-win situation, am I right?
The Secret Sauce of Secure Inventory Sharing Protocols
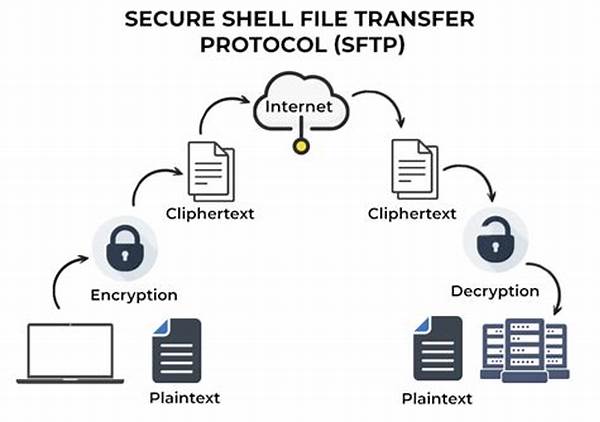
So, let’s spill the beans on what makes these protocols so dope. First up, you’ve got encryption. It’s like putting your data in an indestructible safe. Only you have the key, and anyone without it is just wasting their time trying to peek inside. These protocols ensure that all the juicy inventory deets are wrapped up tighter than a burrito.
Then, there’s authenticity. Secure inventory sharing protocols ensure the info is coming from where it should be, not from some random dude trying to mess with your game. It’s like checking out a band’s official channels for their latest tracks, instead of getting duped by some fake remix off-brand site.
And let’s not forget about verification! Every time stock info is shared, it gets validated like a golden ticket to Willy Wonka’s factory. No fakes here, just the genuine, top-shelf stuff. This means you can get hyped about knowing what you’re dealing with is 100% legit.
Breaking Down the Magic of Secure Inventory Sharing Protocols
1. Trust: It’s like a warm hug from a good friend, only digital. Secure inventory sharing protocols make sure everyone plays fair.
2. No Sneak Peeks: Your inventory details get the VIP treatment. Absolutely no uninvited guests.
3. Win-Win: Companies share without fear of backstabbing. Everybody gets a fair share of the pie.
4. Chill Vibes: No need to stress because everything’s encrypted and safe. It’s like having a Zen garden for your data.
Read Now : Blockchain Innovation Trends At International Events
5. Easy Breezy: These protocols streamline processes, making everything smooth like butter. No one has time for drama!
How Secure Inventory Sharing Protocols Drive Business Success
Imagine a world where every shred of inventory data you had was secure and shared effortlessly. Sounds like a dream, right? Secure inventory sharing protocols make that dream a reality. They are the unsung heroes—doing the behind-the-scenes work that makes everything tick harmoniously.
Businesses get to harness the full potential of partnerships and never miss out on opportunities. No more worrying about potential mix-ups or leaks. It’s like having an A-team of professional bouncers guarding your VIP data party. Knowing that secure inventory sharing protocols are in place lets companies get back to the serious business of smashing goals and making waves.
Sharing becomes not just a necessity but a celebration. Think of secure inventory sharing protocols like the glue that keeps everything together. Companies can focus on what they do best while staying confident in their secure, shared future.
Embracing the Future with Secure Inventory Sharing Protocols
We’re living in a time where secure inventory sharing protocols aren’t just a want—they’re a need. Businesses are diving headfirst into this new era of sharing, networking, and collaborating like never before. And why not? When you’ve got protocols that slick, who wouldn’t want to join the party?
Companies that embrace these protocols are like surfers catching the biggest, baddest waves. They’re ahead of the game, riding high on the crest of technology and innovation. With secure inventory sharing protocols, everyone’s got a chance to ride that wave and live out their business fantasies.
It’s a brave new world out there with secure inventory sharing protocols leading the charge. Who knows what else is possible when companies commit to smart sharing?
Wrapping Up the Secure Inventory Sharing Protocols Adventure
So, in the end, here’s the lowdown. Secure inventory sharing protocols aren’t just some fancy tech jargon. They’re the real MVPs in business circles today. They keep everything tight, make sharing a breeze, and ensure everyone plays nice in the sandbox.
Each time a company adopts these protocols, it’s like adding a shiny, new tool to their toolkit. It’s safe, it’s smart, and it’s future-forward. As more people jump on the bandwagon, it’s time we all start thinking about how secure inventory sharing protocols can make our business lives just a tad bit more epic.
Remember, in this world of ever-evolving tech, staying ahead of the pack means being open to new ways of working. With secure inventory sharing protocols, the future is bright, safe, and downright thrilling!