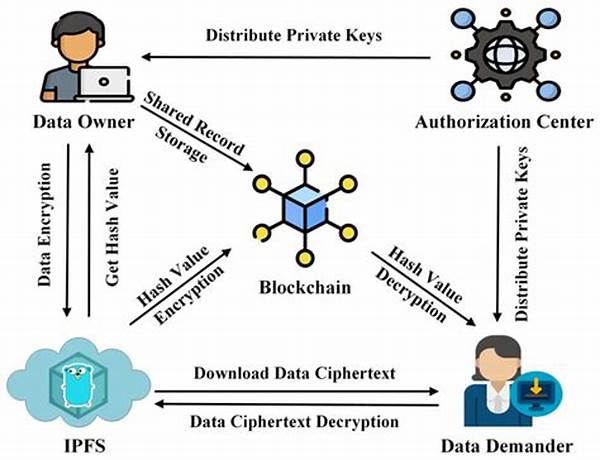
Once upon a time, in the bustling tech city of Byteville, data flowed like rivers between towers of firewalls and encryption. Companies traded information like ancient merchants, each vying for smarter and faster ways to keep their data safe. Amidst the chaos and constant cyber threats, a group of engineers cooked up something revolutionary—secure shard data exchange methods. This innovative approach promised to mend the fractures of security breaches with its genius and form an impenetrable fortress for sensitive data.
Read Now : Blockchain Innovation For Inclusive Society
The Magic of Secure Shard Data Exchange
So, let’s dig deeper into what makes these secure shard data exchange methods tick. Picture this: your data is like a precious gemstone. Instead of flaunting the whole bling, you cut it into several pieces, or shards, and spread them around. Each shard doesn’t make sense on its own and requires the others to shine in full glory. This means that even if some cyber sneak manages to nab a shard or two, they still can’t crack the code. That’s the genius of secure shard data exchange methods—keeping secrets secret even when pieces are out in the open.
Imagine trying to complete a jigsaw puzzle without all the pieces. Frustrating, right? That’s the power of secure shard data exchange methods. They’re like spreading rumors but keeping just enough to yourself to leave everyone guessing. In a world where data breaches are the boogeymen, these methods are the sturdy locks keeping the horrors at bay. They aren’t rocket science, but they sure manage to keep digital bandits scratching their heads.
Five Groovy Elements of Secure Shard Data Exchange
1. Dynamic Sharding: Data isn’t just clumped together; it’s split dynamically. It’s like a disco dance—always moving and unpredictable.
2. Encryption Pizzazz: Even the shards get a taste of glamour with top-notch encryption. It’s like putting a lock within a vault.
3. Access Control Mojo: Only the right peeps get the full picture. Secure shard data exchange methods play bouncer with style.
4. Efficient Tracking: Every shard’s journey is tracked, making sure they’re not hitching rides with unwanted guests.
5. Self-Destruct Protocols: Unused shards go kaboom! Okay, not literally, but they vanish after their purpose is fulfilled.
Why Secure Shard Data Exchange Methods Matter
Back in the day, data was secure if it had strong passwords and good encryption. Now? That’s ancient history, folks. Enter secure shard data exchange methods, the superheroes of data security. They’re the cool kids who pull off the seemingly impossible.
Consider them the Sherlock Holmes of data protection, always one step ahead of the cyber criminals. Data is broken into shards, scattered, and monitored, making it a wild goose chase for anyone trying to be naughty with it. Plus, with added layers of encryption and access protocols, even the bravest hacker might reconsider. Talk about a win-win! Secure shard data exchange methods have flipped the script for how we perceive data safety, holding a shiny promise for a more secure digital universe.
Read Now : Tokenization And Digital Assets Management
Taking Secure Shard Data Exchange to the Next Level
So, you’re probably thinking, how do you supercharge those secure shard data exchange methods? It’s all about being tech-smart. First, embrace next-gen encryptions like bees to honey. They’re sophisticated enough to keep intruders puzzled. Layer it up with smart AI algorithms that can recognize and adapt to threats faster than you can say “cyber!”
Moreover, collaboration is key. Think of it like a digital potluck, where everyone brings their best dish—except you’re exchanging the best strategies and insights to bolster data protection. Finally, always play the game of updates. Secure shard data exchange methods thrive on the latest software patches and tweaks. They’re the booster shots that keep data strong and resilient.
Tales of Triumph with Secure Shard Data Exchange Methods
In a data-driven world, everyone wants peace of mind. Secure shard data exchange methods aren’t just a bunch of confusing tech terms; they’re success stories waiting to be told. Businesses can sleep easy knowing their secrets are closer to being Fort Knox level.
Imagine a world where data breaches are as rare as unicorns in your backyard. Impossible? Not quite. With secure shard data exchange methods, we’re inching closer to that dream world. They’ve rewritten the rulebook on data protection, showing us all that it’s possible to stare down data thieves and grin victoriously. It’s the dawn of a secure day, and we’re all invited to bask in its glory.
Living the Secure Shard Dream
Living in a world with secure shard data exchange methods is like having a robust digital guardian angel on speed dial. It’s a kind of assurance that brings great relief to businesses and individuals alike. Imagine having your secrets black-boxed, scattered, and living harmoniously in a digital symphony. Cool, right?
It’s the future many have been yearning for! Digital citizens can stroll through the web, confident and carefree. Of course, it takes some nifty tech juggling to maintain this sense of security—but then again, nothing strong comes without its trials. Secure shard data exchange methods are not merely tech innovations; they’re a revolution that has redefined data protection’s status quo.