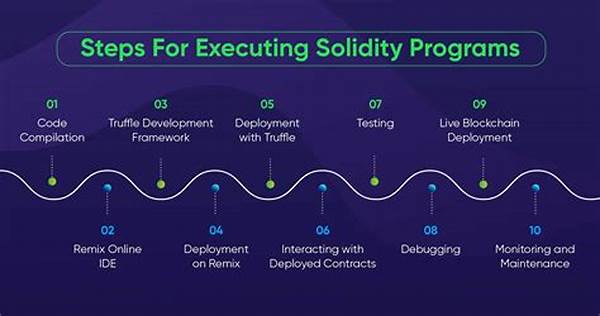
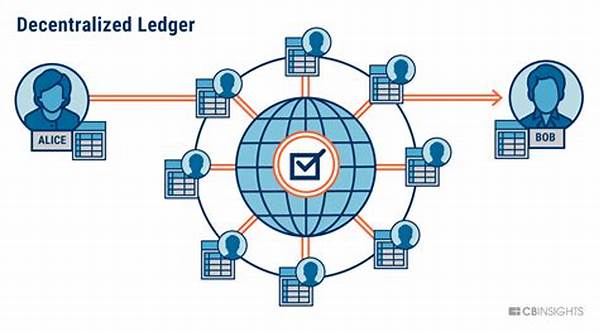
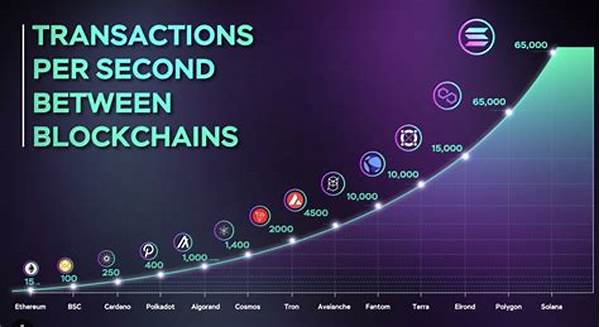
Once upon a time, in the bustling world of blockchain development, there was a young coder named Alex. Alex was passionate about creating decentralized applications that could change the world. However, he knew the road to secure and efficient smart contracts was paved with potential pitfalls. One day, while hunched over his computer with a cup of coffee in hand, Alex stumbled across the ultimate guide: “Secure Solidity Programming Guidelines.” This treasure trove of wisdom promised to make his code bulletproof, and he was determined to unlock its secrets.
Read Now : Intellectual Property Theft Prevention
Getting to Know Secure Solidity Programming Guidelines
Alright, buckle up, tech-savvy friends! We’re diving into the glamorous world of secure solidity programming guidelines. Picture this: you’re deep into building the next big thing on Ethereum, but security is key. With so many hackers lurking around, it’s like trying to navigate a minefield. But don’t worry, these guidelines are your trusty map.
The first rule is all about knowing your tools. Solidity isn’t just a coding language; it’s a whole new beast. You’ve gotta get comfy with it, and that means understanding each quirk and its built-in security features. Solidity’s like that cool kid at school who knows all the shortcuts but also gets you into trouble if you’re not careful.
Then there’s this little thing called overflows. You know, when your numbers go so big they break the internet — and not in a cute puppy video way. Secure solidity programming guidelines are gonna help you keep those pesky overflows in check. And let’s not forget testing — it’s your bread and butter. Double-check everything, because nobody likes surprise bugs. Stick with these guidelines, and you’ll be the blockchain hero in no time!
The Essentials of Secure Solidity Programming Guidelines
1. Know Your Environment: Ethereum is not just a platform; it’s an ecosystem. The secure solidity programming guidelines always remind us to explore and understand every facet of it.
2. Code Clarity: Write clean, understandable code. Secure solidity programming guidelines want your future self and fellow coders to high-five you for it.
3. Avoid Hardcoding: This one’s big — don’t lock constants in your code. Secure solidity programming guidelines suggest using configurations instead for flexibility.
4. Gas Efficiency: Secure solidity programming guidelines say be smart with gas usage to keep costs low and performance high.
5. Regular Audits: These are like health check-ups for your code. Stick to secure solidity programming guidelines, and audit often to catch sneaky vulnerabilities.
Secure Solidity Programming Guidelines in Action
Now, let’s talk about how secure solidity programming guidelines work their magic in real-world applications. When you’re knee-deep in code, these guidelines are like the best sidekick ever. Because guess what? Murphy’s Law loves to visit coders — anything that can go wrong will go wrong.
When you’re building smart contracts, the stakes are high. One tiny slip-up, and a hacker could swoop in faster than a seagull on a hot chip. But don’t sweat it! Secure solidity programming guidelines are your force field, your superhero cape. They’re here to ensure you don’t end up on the evening news as “that coder who lost millions.”
Diving Deeper into Secure Solidity Programming Guidelines
In this chapter, we’re dialing up the wizardry level a notch. With the secure solidity programming guidelines, you’ve got a magical checklist to weave enchantment into your code. Pop quiz: what’s the most overlooked threat? Spoilers, it’s reentrancy attacks! These sneaky little devils can mess up your contract, but fear not. Proper guidelines cover all.
Now, guard those funds like they’re gold-plated hotcakes. Everyone loves a solid wallet, right? Secure solidity programming guidelines keep your crypto assets safe, sound, and snazzy. And while we’re at it, let’s talk ownership — control is everything, bae. These guidelines make sure you know who’s in the driver’s seat of your smart contract.
Read Now : “supply Chain Risk Management”
Oh, and remember our surveyor’s tip: test, test, and test again! The secure solidity programming guidelines make testing as crucial as coffee is to coding marathons. So, stay curious, tap into those guidelines, and strut through your blockchain journey like the rockstar you are.
A Deeper Analysis of Secure Solidity Programming Guidelines
You know, without the secure solidity programming guidelines, coding would be like walking on a tightrope while juggling flaming swords. They’re your safety net, ensuring you don’t accidentally create the digital version of the Titanic. Because, let’s face it, nobody wants that.
These guidelines are your best bud when it comes to mastering the fine art of crafting flawless Ethereum dApps. They whisper safety secrets like, “Psst, use ‘SafeMath’ for calculations, or you’ll end up breaking the blockchain.” Plus, they’re like the ultimate cheat sheet for writing efficient code that’ll have your peers nodding in approval.
Your blockchain journey isn’t going to be all smooth sailing, trust us. But with secure solidity programming guidelines, you’re not alone. You’ll discover how to sniff out vulnerabilities before they become ticking time bombs. You’ll become the hero coder everyone needs — like the blockchain guardian angel you were born to be.
What Secure Solidity Programming Guidelines Mean for Developers
Here’s the scoop on secure solidity programming guidelines: they’re less about preaching and more about empowering you. With these top-notch guidelines, you’re not just coding — you’re crafting an ironclad fortress. Every line of code counts, and you’ve got the cheat codes in hand.
Imagine being a part of something legendary. Picture yourself at the helm of a cutting-edge project. These secure solidity programming guidelines are like unlocking secret levels in a game — and trust us, the rewards are worth it. A community of like-minded developers will follow your lead, applauding every secured smart contract you push out.
Don’t see these guidelines as rules that rain on your parade. They’re more like the whimsical road signs you need on your path to success. With secure solidity programming guidelines by your side, you’re slaying bugs, ensuring security galore, and most importantly, delivering results that’ll make your mama proud.
Wrapping Up Secure Solidity Programming Guidelines
As our journey through the world of secure solidity programming guidelines comes to a close, it’s clear these aren’t just mere rules to follow. They’re the game’s secret sauce, the ultimate ticket to crafting top-tier smart contracts. From battling bugs to thwarting hackers, these guidelines hold the map to blockchain glory.
So, fellow coder, you’ve discovered the magic formula. Now go boldly into the blockchain frontier, guided by secure solidity programming guidelines. You’re not just another coder; you’re a digital pioneer. With these guidelines, your contracts are set to be cornerstone works, admired by a community that values security above all else.
In the end, what’s better than knowing you can develop with confidence, peace of mind, and, most importantly, with security as your trusty sidekick? Let these secure solidity programming guidelines be your guiding light — and go claim your place in the blockchain history books.