Once upon a time in the bustling city of Tradeopolis, there was a legendary puzzle known as the great supply chain maze. Entrepreneurs and business moguls alike spoke in hushed tones of the secret to navigating this intricate network. Enter Alex, a young and savvy operations manager determined to crack the code. Armed with determination and a keen sense of adventure, Alex was about to uncover the magic of secure supply chain management practices.
Read Now : Tokenized Virtual Reality Assets
The Rise of Online Security in Supply Chains
Picture this: Alex is knee-deep in paper contracts and email trails, battling data breaches with nothing but a laptop and WiFi. The shift to digital wasn’t just a fancy tech upgrade; it was the dawn of a new era. As companies got woke to cybersecurity threats, secure supply chain management practices became the unofficial hype of corporate corridors. In today’s wild world, it’s like every click has consequences, and Alex found out fast how online security was the lock and key to a seamless supply chain.
Once just fancy jargon, these practices are now the real MVPs, offering peace of mind like a warm cup of tea on a winter day. With secure supply chain management practices, companies saved money and resources while dodging potential disasters. It’s like dodging those nasty potholes on life’s highway: smooth ride guaranteed. For Alex, it wasn’t just about running a tight ship but also knowing when to batten down the hatches.
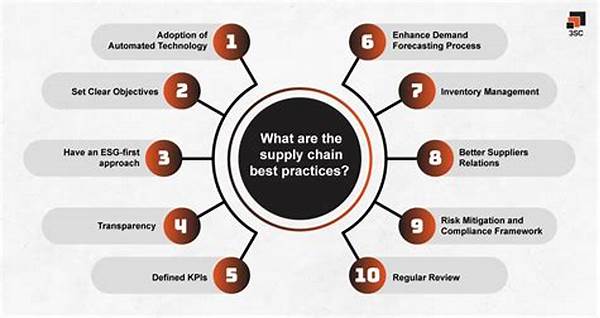
Key Steps to Strengthen Your Supply Chain
1. Encryption Icon: Guard your data with Fort Knox level encryption, because nobody’s got time for prying eyes in their docs.
2. Vendor Vetting: Get real picky with who supplies your goods. Their sketchy practices can bring down the whole tower.
3. Secure Networks: Use networks so secure a hacker would sweat buckets trying to break in. It’s like the money heist but without the drama.
4. Regular Audits: Keep your system under the microscope with regular audits. If your processes were a gym bod, think of audits as the personal trainers keeping it tight.
5. Emergency Plans: When stuff hits the fan, your panic button toolkit (aka emergency plans) should be your best friend. Don’t leave home without ’em.
The Cybersecurity Balancing Act
As Alex dived headfirst into the chaos, one thing was clear: cybersecurity wasn’t just for IT geeks anymore. It was everyone’s gig. Secure supply chain management practices meant knowing your enemies, testing defense lines, and staying a step ahead. Imagine it like a giant chess game with the stakes being your company’s reputation. Queen to D5, protect that data!
Balancing between efficiency and vigilance was like walking a tightrope, and Alex felt every wobble. But mastering the art of secure supply chain management practices meant syncing up teams, brainstorming zillions of possible scenarios, and thinking like hackers but with ethics. After all, the goal was keeping the trade winds favorable while blocking out the cyber pirates.
Securing Vendor Relationships
In the land of supply chains, trust isn’t handed out like candy. Alex learned the hard way that partnerships could make or break the fortress of secure supply chain management practices. Every vendor, every handshake, needed that extra layer of scrutiny. Do they treat data like royalty? Are their processes as foolproof as a James Bond escape plan?
Read Now : Top Blockchain Summits Dubai 2023
Building alliances meant getting chummy with compliance standards and maybe even literal handshakes. Secure supply chain management practices were the backbone of this dance. It was about creating a network so solid, even Loki couldn’t find a loophole. Alex knew that a fortified supply chain wasn’t just about keeping the products flowing; it was about weaving a story of trust and reliability.
The Role of Technology in Supply Chain Security
Let’s face it; tech is the fairy godparent Alex never knew they needed. With the rise of AI, blockchain, and IoT, secure supply chain management practices were no longer a shot in the dark. Emerging tech turned threats into trash talk and vulnerabilities into valiant victories. Imagine turning data breaches into pixelated fairytales no longer haunting the supply chain kingdom.
Technology threw a spotlight on weak links and transformed them into robust, knight-like defenders. Alex harnessed the power of real-time data and AI predictions, effectively banishing shadowy threats trying to sneak in the backdoor. It was tech’s version of a magical shield, and secure supply chain management practices were the spell Alex needed to cast.
From Chaos to Control
The beauty of secure supply chain management practices lay not just in what it achieved—but in how it transformed operations from chaos into a symphony. Trust was no longer an abstract concept but a tangible asset. The power to predict, protect, and prevent reshaped Alex’s approach to a business dynamic as unpredictable as a soap opera plot twist.
In the end, secure supply chain management practices didn’t just safeguard trade routes. They taught Alex the art of resilience. Whether it was learning from a notorious breach or fortifying relationships, every step added a new layer of control. And Alex, much like the city of Tradeopolis, thrived knowing their supply chain wasn’t just a checklist; it was a legacy of security written with every transaction.
Conclusion: The Journey Continues
So, what’s the takeaway here? Secure supply chain management practices are like the unsung heroes of commerce tales—the Gandalf to every Frodo’s perilous trek. While the road to mastering them might be rocky, the peace of mind they bring is golden. Alex’s journey reveals that the only constant is change and the beauty of staying one step ahead in an ever-evolving landscape.
Secure supply chain management practices are more than just a trend or a best practice. They’re the guiding star in a night sky of uncertainty. As Alex would say, it’s not just about moving products from point A to B but ensuring they arrive safely and securely every step of the way. And so, the story continues, with secure supply chain tricks up everyone’s sleeves and a world ready to meet the future head-on.